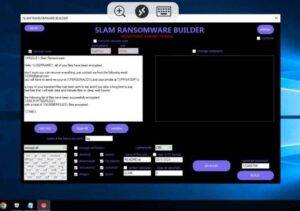
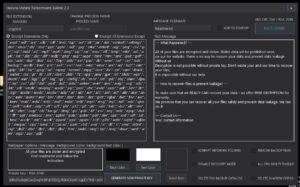
Introduction to Slam Ransomware Builder In the ever-evolving landscape of cybersecurity, new threats emerge regularly, challenging the defenses of even the most secure systems. One such emerging threat is the Slam Ransomware Builder. This blog post aims to provide an in-depth understanding of what it is, how it operates, and the potential risks it poses.

All posts in "Malwares"
103
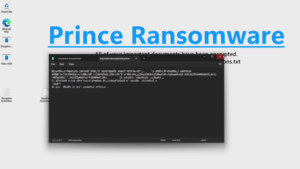
July 5, 2024Brief Overview Prince is a ransomware written from scratch in Go. It uses a mixture of ChaCha20 and ECIES cryptography in order to encrypt files securely so that they cannot be recovered by traditional recovery tools. Files which have been encrypted by Prince can only be decrypted using the corresponding decryptor. Installation & Setup Pre-requisites:
191
June 29, 2024The WannaCry ransomware attack was a worldwide cyberattack in May 2017 by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency. It was propagated by using EternalBlue, an exploit developed by the United States National Security Agency (NSA) for Windows systems. EternalBlue was stolen and leaked by a group called The Shadow Brokers a month prior to
- June 29, 2024
Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used
245
June 22, 2024The MOST powerful stealer (Cookie stealer, Discord token stealer, Roblox stealer, Password stealer, Credit card stealer, Autofill stealer, Steam stealer) Much MORE Features 🎮 – Steal Steam Credentials, Riot games, Roblox, Minecraft session, Epic games, uplay, Growtopia 🔒 – Bypass Better Discord and Discord Token Protector 🖼️ – Custom icon🤖 – Website Cookie Information (Spotify,
310
June 21, 2024Horus Eyes RAT (HE-RAT) is a tool used by cybercriminals to bypass security mechanisms. It has been used in high-profile activities, such as the Warsaw banking trojan, which tricks victims into infecting their systems using a fake bank overlay window. HE-RAT has the following features: Persistence, Gathering details, Capturing data, Matching data, and Executing remote commands. one of the
- June 17, 2024
Powerful multi-platform stealer with a huge pack of grabbed data. Wallets stealer, browsers stealer, sessions stealer, etc. All logs will be sent using discord webhooks or telegram bot. Data grubed Introduction to the Murk Stealer The digital landscape is constantly evolving, bringing with it both opportunities and threats. Among the latest cybersecurity threats is the
353
June 13, 2024Introduction to Liberum Screen Rat V1.8 Liberum Screen Rat V1.8 is an advanced tool meticulously crafted for efficient screen management and monitoring. This software is designed to address a myriad of challenges faced by IT professionals, network administrators, and businesses striving to optimize their screen usage. By providing real-time monitoring and comprehensive control over multiple
236
June 10, 2024The latest edition of this software is beautifully established, that can help you to encrypt documents on the inflamed device. It allows the users to display a message to inform other users that their files are locked. Cybercriminals can demand a fee from their targets to restore their data, and in this way after they
255
June 9, 2024Features :CosaNostra v1.2 HTTP BotNet + Tutorial Can : Thief Files (Photos, Documents, TXT)Download and run (loader)Get Information Device Get location and addressClear cookies and sessions from 20 browsers such as Anti-Sandbox like
177
June 8, 2024The developer has created a tool that can build malicious CPLApplet programs. The following features are available in the builder: ✅ injection in explorer.exe✅ Hidden schtasks✅ WDExcluion✅ Anti Analysis✅ Offline – Online✅ Change Path✅ Super Hidden Tutorial Video : Play
142
June 5, 2024PAID BOTNET LESSONS 🔸 Centos 6 VPS Setup (VIDEO)🔸 Centos 7 VPS Setup (VIDEO)🔸 Virutal Machine Setup (VIDEO)🔸 Disable Windows Defender (VIDEO)🔸 Domain Setup🔸 Betabot 1.8.0.11 Botnet Setup (VIDEO)🔸 Zyklon 1.3 Botnet Setup (keylogger) (VIDEO)🔸 Azorult 3.1 Botnet Setup (stealer) (VIDEO)🔸 WorldWind Setup And Tutorial (stealer) (VIDEO)🔸 RAT Setup (DNS and Tool )🔸 Crypting (Common
180
May 28, 2024PendroidLocker Latest Version 2024 + Old VersionYou can choose freely between the latest version and the old one, which I still think is the best. Plus, setup video included Need: Java JDK, Android Studio 4, Hosting
80
May 25, 2024Conti ransomware is one of the most prolific malware strains in the global cyber threat landscape. Conti has cost organizations more than $150 million in ransom fees since 2020 and has affected more than 1,000 businesses worldwide. Conti is a second-stage malware attributed to the Wizard Spider group. It is believed to be the successor to the prolific Ryuk ransomware.
320
May 5, 2024Password: linuxndroid 👻Hidding After Deletion ⚙️Bypass Google Play Antivirus 🖥️Live Screen ( Advance screen Mirror) Unlock All Screen Locks Advance Injection😈Inject Virus to Apks 🔰Target wallet Usdt Hack automatically ✔️No restrictions on use ✔️Secure Connection No disconnection 📲 Support Banking Apps And Digital CryptocurrencyWithout Blanking out your Screen
44
May 2, 2024An undetectable stealer software at both runtime and scan time. It operates asynchronously, ensuring complete stealth (FUD). It steals passwords, cookies, autofill data, sessions, and tokens. Capable of targeting platforms like Instagram, Twitter, TikTok, Twitch, Spotify, Riot Games, Reddit, Roblox, and Steam. 😱 Features : 📃 Fake Error.📷 Capture Screenshot.📶 WiFi Stealer.🔒 Create Mutex.📲 Discord
- April 23, 2024
The Spyroid Rat offers a wide array of functionalities to manage and monitor Android devices discreetly. From file and call management to live location and screen tracking, SMS and application management, keylogging, social media account hacking, and more, Spyroid Rat is designed for stealthy control, presenting a significant threat to Android device security and privacy. Advanced
58
April 16, 2024Password: CrackMasterHub It is the latest version of private RAT called Xworm. ⭐️ COMPILING: Download all source files, launch builder and fill in all gaps New Features: 💠 More than 69+ Features in this Tool
132
March 14, 2024XWorm 5.6 RAT . FUD Rat Builder & Open SRC This is not a crack and not a reverse either. XWorm Rat Source codes have been completely leaked. There are so many shitty Rat, XWorm is one of them. I’m sharing it so that you don’t pay for such things for nothing Password: Z9jRDojoLE07biIrFqAw
436
March 11, 2024Features: ✓ Crypto injections :Trustwallet, Metamask, Exodus wallet, Binance, Kucoin, Bybit, Coinbase exchange, Coinbase wallet, Huobi global, Blockchain, Kraken.✓ Show Scam page : Direct display scam page on screen to grabbs data in real time✓ Injection : This will show scam page everytime when user want to open injected wallet✓ PIN & Pattern lock grabbs