CVE-2023-50254: PoC Exploit for Deepin-reader RCE that affects unpatched Deepin Linux Desktops. Deepin Linux’s default document reader “deepin-reader” software suffers from a serious vulnerability due to a design flaw that leads to Remote Command Execution via crafted docx document.
Details
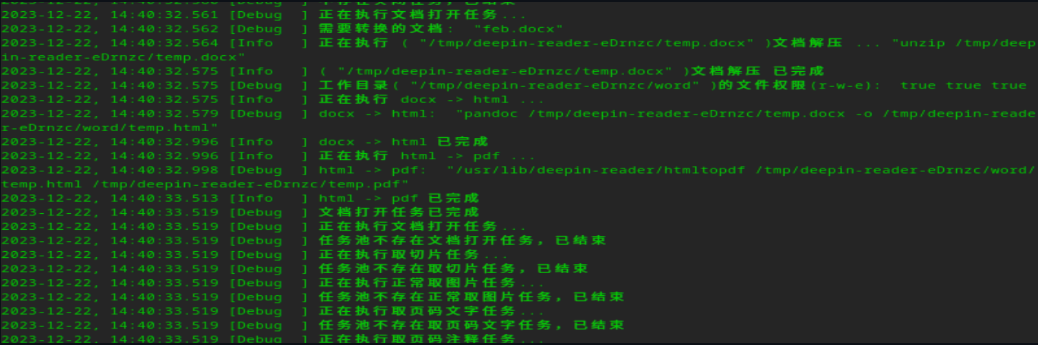
Deepin-reader is the default document reader for the Operating System Deepin Linux. The deepin-reader performs some shell command operations while dealing with docx document format.
- When opening a docx document , deepin-reader creates a temporary directory under /tmp and places the docx document under the directory
- Then deepin-reader calls the “unzip” shell command to extract the docx file
- After the extraction process, deepin-reader calls “pandoc” command to convert the docx file to an html file named “temp.html” under word/ directory (created when the docx file is extracted with unzip). The command will look something like this, “pandoc temp.docx -o word/temp.html
- Then deepin-reader will try to convert that HTML file to pdf and open the pdf.





What do you think?
It is nice to know your opinion. Leave a comment.