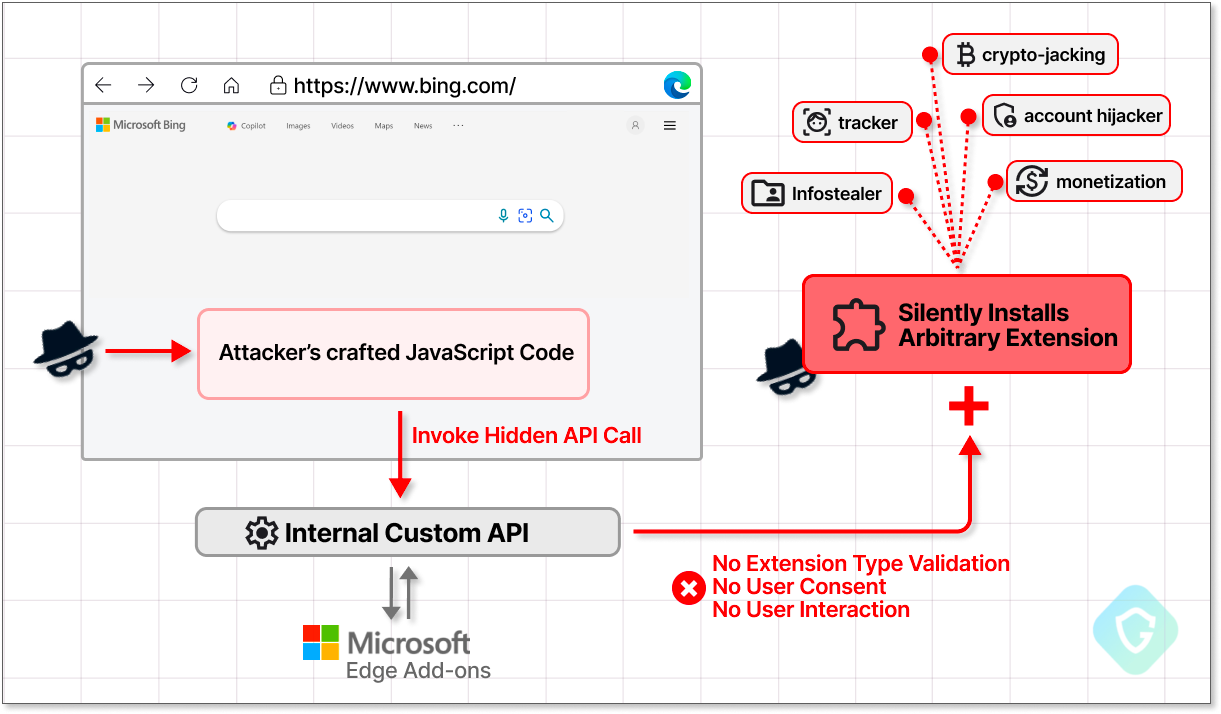
Guardio Labs discovered a vulnerability in Microsoft Edge, designated CVE-2024–21388. This flaw could have allowed an attacker to exploit a private API, initially intended for marketing purposes, to covertly install additional browser extensions with broad permissions without the user’s knowledge. The vulnerability was promptly disclosed to Microsoft, leading to a resolution in February 2024. https://labs.guard.io/cve-2024-21388-microsoft-edges-marketing-api-exploited-for-covert-extension-installation-879fe5ad35ca
The vulnerability enables anyone with a method to run JavaScript on bing.com or microsoft.com pages to install any extensions from the Edge Add-ons Store without the user’s consent or interaction. This is an “Elevation of Privilege” issue classified as Moderate in severity by the Microsoft Security Response Center (MSRC).
Exploit Method
The script utilizes a private browser API accessible from privileged Microsoft websites to install any desired extension silently, bypassing user consent. By injecting a script into the context of a privileged website like bing.com, the exploit triggers the installation of the selected extension without user interaction.
Usage
- Ensure Python is installed on your system.
- Clone the repository and navigate to the exploit script.
- Edit the script to specify the target extension ID and manifest.
- Execute the script using Python.





What do you think?
It is nice to know your opinion. Leave a comment.