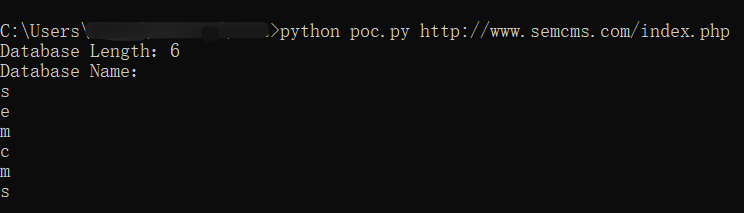
A SQL injection vulnerability exists in SEMCMS v4.8. The vulnerability stems from a lack of validation of externally entered SQL statements in the web_inc.php parameter languageID. An attacker with no credentials can use this vulnerability to execute illegal SQL commands to obtain sensitive data from the database.
Vulnerability analysis
The vulnerability exists on line 83 of web_inc.php:
if (isset($_POST["languageID"])){
$Language=test_input(verify_str($_POST["languageID"]));
}else{
$Language=verify_str($Language);
}




What do you think?
It is nice to know your opinion. Leave a comment.