CVE-2024-20656 is a security vulnerability that affects Visual Studio and was released on January 9, 2024. It is a local privilege escalation vulnerability in the VSStandardCollectorService150 service.
With this we have all pieces for our exploit, to summarise:
- Create a dummy directory where the VSStandardCollectorService150 will write files.
- Create a junction directory that points to a newly created directory.
- Trigger the VSStandardCollectorService150 service by creating a new diagnostic session.
- Wait for the
<GUID>.scratchdirectory to be created and create new object manager symbolic linkReport.<GUID>.diagsessionthat points toC:\\ProgramData. - Stop the diagnostic session.
- Wait for the
Report.<GUID>.diagsessionfile to be moved to the parent directory and switch the junction directory to point to\\RPC Controlwhere our symbolic link is waiting. - Sleep for 5 seconds (not really important but left it there).
- Switch the junction directory to point to a dummy directory.
- Start a new diagnostic session.
- Wait for
<GUID>.scratchdirectory to be created and create a new object manager symbolic linkReport.<GUID>.diagsessionthat points toC:\\ProgramData\\Microsoft - Stop the diagnostic session.
- Wait for the
Report.<GUID>.diagsessionfile to be moved to parent directory and switch the junction directory to point to\\RPC Controlwhere our symbolic link is waiting. - After the permissions are changed we delete the
C:\\ProgramData\\Microsoft\\VisualStudio\\SetupWMI\\MofCompiler.exebinary. - Locate and run the
Setup WMI providerin repair mode. - Wait for our new
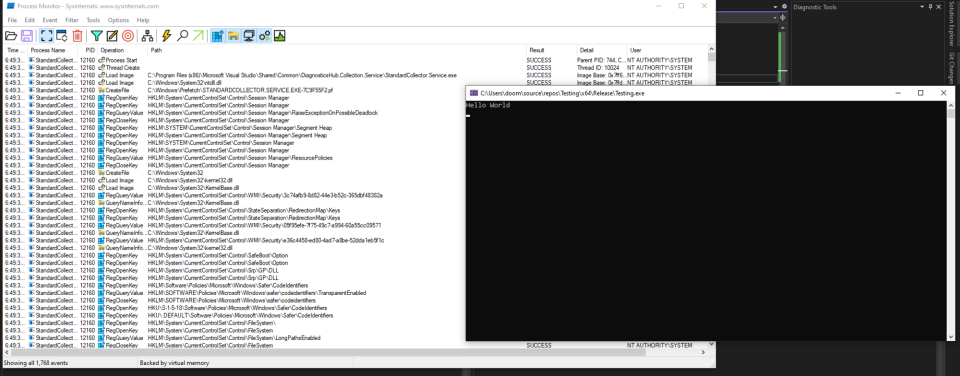
MofCompiler.exebinary to be created by the installer and replace it with cmd.exe - Enjoy SYSTEM shell 🙂





What do you think?
It is nice to know your opinion. Leave a comment.