WAF bypass Tool is an open source tool to analyze the security of any WAF for False Positives and False Negatives using predefined and customizable payloads. Check your WAF before an attacker does. WAF Bypass Tool is developed by Nemesida WAF team with the participation of community.
Payloads
Depending on the purpose, payloads are located in the appropriate folders:
FP – False Positive payloads
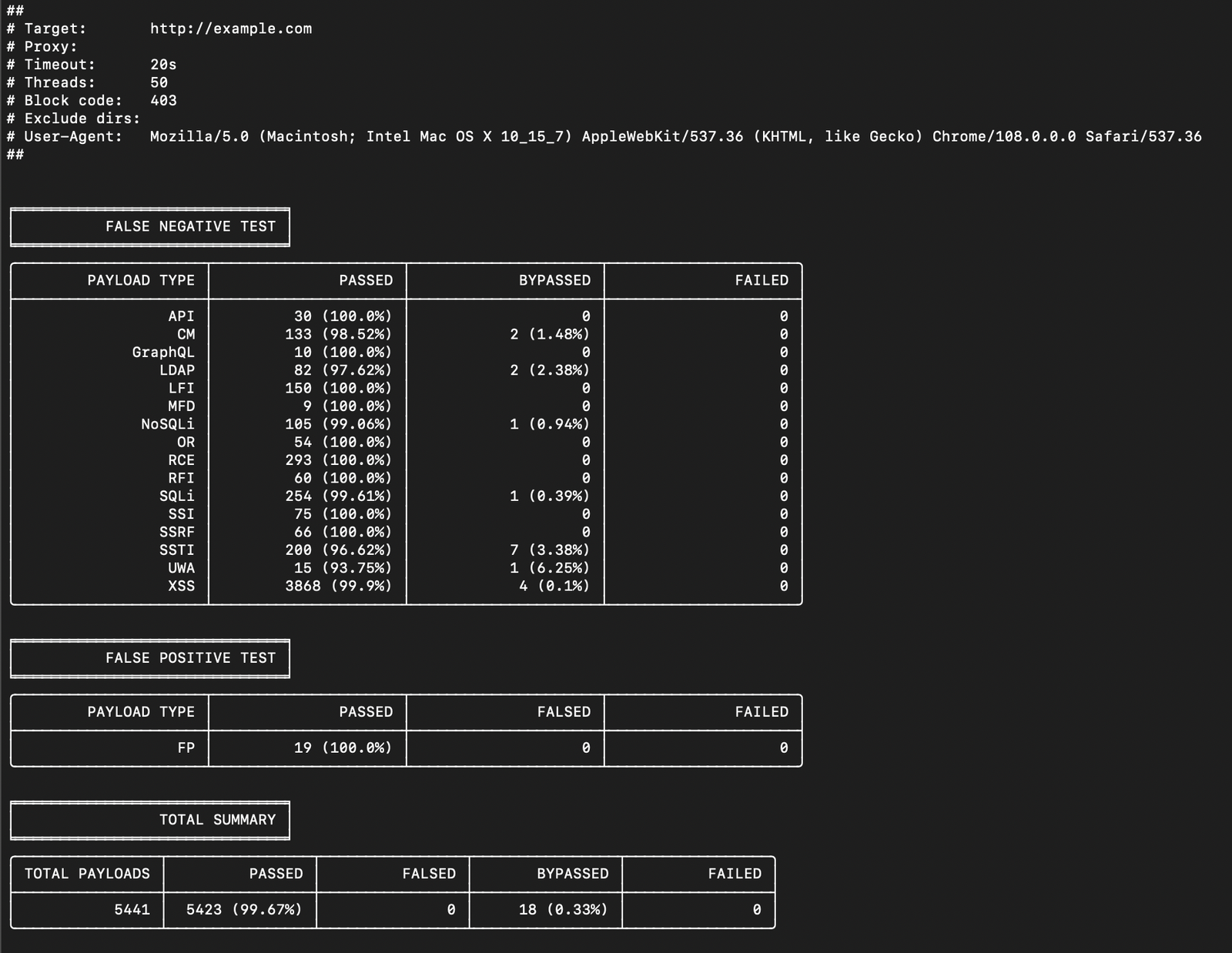
API – API testing payloads
CM – Custom HTTP Method payloads
GraphQL – GraphQL testing payloads
LDAP – LDAP Injection etc. payloads
LFI – Local File Include payloads
MFD – multipart/form-data payloads
NoSQLi – NoSQL injection payloads
OR – Open Redirect payloads
RCE – Remote Code Execution payloads
RFI – Remote File Inclusion payloads
SQLi – SQL injection payloads
SSI – Server-Side Includes payloads
SSRF – Server-side request forgery payloads
SSTI – Server-Side Template Injection payloads
UWA – Unwanted Access payloads
XSS – Cross-Site Scripting payloads



What do you think?
It is nice to know your opinion. Leave a comment.